Proxmox VE
What is Proxmox VE
Proxmox Virtual Environment is an open source server virtualization management solution based on QEMU/KVM and LXC. You can manage virtual machines, containers, highly available clusters, storage, and networks with an integrated, easy-to-use web interface or via CLI. Proxmox VE code is licensed under the GNU Affero General Public License, version 3. The project is developed and maintained by Proxmox Server Solutions GmbH.
Requires Proxmox VE 7.0 or newer.
Preparation
The following placeholders will be used:
proxmox.companyis the FQDN of the Proxmox VE server.authentik.companyis the FQDN of the authentik install.
authentik configuration
-
In the Admin interface, navigate to Applications -> Providers to create an OAuth2/OpenID provider with these settings:
- Name: proxmox
- Redirect URI:
https://proxmox.company:8006(No trailing slash, include the web interface port) - Signing Key: Select any available key
-
Create an application using the provider.
- Under Applications > Applications in the Admin interface, create a new application and configure it to use the provider created in the previous step.
- Optionally, apply access restrictions to the application.
- Set the Launch URL to
https://proxmox.company:8006.
Proxmox VE configuration (using the web interface)
-
Log in to the Proxmox VE web interface using an administrative account.
-
Navigate to authentication source settings.
- Go to Datacenter > Permissions > Realms.
- Click Add and select Realm to open the Add Realm dialog.
-
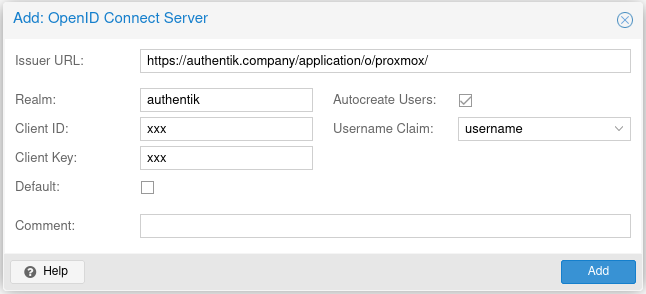
Fill out the OpenID Connect settings.
- In the dialog that appears, fill in the following details:
- Issuer URL: Enter the Issuer URL from authentik (found in your provider's overview tab), e.g.,
https://authentik.company/application/o/proxmox/. - Realm: Enter a name for this authentication source, such as
authentik. - Client ID: Enter the Client ID found on the provider overview page.
- Client Key: Enter the Client Secret. (To find this value click Edit on the Provider overview page.)
- Username claim: Set this to
username. - Autocreate users: Check this box if you want Proxmox to automatically create users upon first login. If checked, users will appear in Proxmox with the format
<authentik username>@authentik. - Default: Check this if you want OpenID Connect to be pre-selected as the default on the login screen.
- Issuer URL: Enter the Issuer URL from authentik (found in your provider's overview tab), e.g.,
Example configuration:
- In the dialog that appears, fill in the following details:
-
Save the configuration.
- Click Add to save the settings.
-
Assign permissions
- After setting up the authentication source, go to Permissions to assign roles and permissions for each user as needed.
-
Logging in
- Users can select this authentication method from the Proxmox login screen, or if set as default, it will be automatically selected.
Proxmox VE configuration (using CLI)
To configure OpenID Connect authentication via the CLI, SSH into any Proxmox cluster node and use the following command:
pveum realm add authentik --type openid --issuer-url https://authentik.company/application/o/proxmox/ --client-id xxx --client-key xxx --username-claim username --autocreate 1